Privacy and AI
We use AI daily on the smartphone that accompanies us everywhere, in the web pages we visit, in the car we drive, in all types of streaming content we consume,… AI is improving our quality of life thanks to personalized services, recommendations adapted to our tastes, greater automation of tasks and processes or more precise and efficient decisions.
Unfortunately, the collection, analysis and use of enormous volumes of information to train and refine AI algorithms is oftenwithout the clear consent of the users and not even their knowledge, can trigger significant threats to our individual privacy.
PETs, to the rescue of privacy
Fortunately, the Privacy Enhancing Techniques (PET), or Privacy Enhancement Techniques, have emerged as a crucial solution to safeguard sensitive information in this digital landscape, providing a balance between the usefulness of AI and the protection of personal data.
PETs are a set of methodologies and approaches designed to ensure that user privacy remains intact despite the intensive use of data by AI systems. These techniques are designed to minimize the amount of personal information that is revealed during users' interaction with intelligent algorithms and systems.
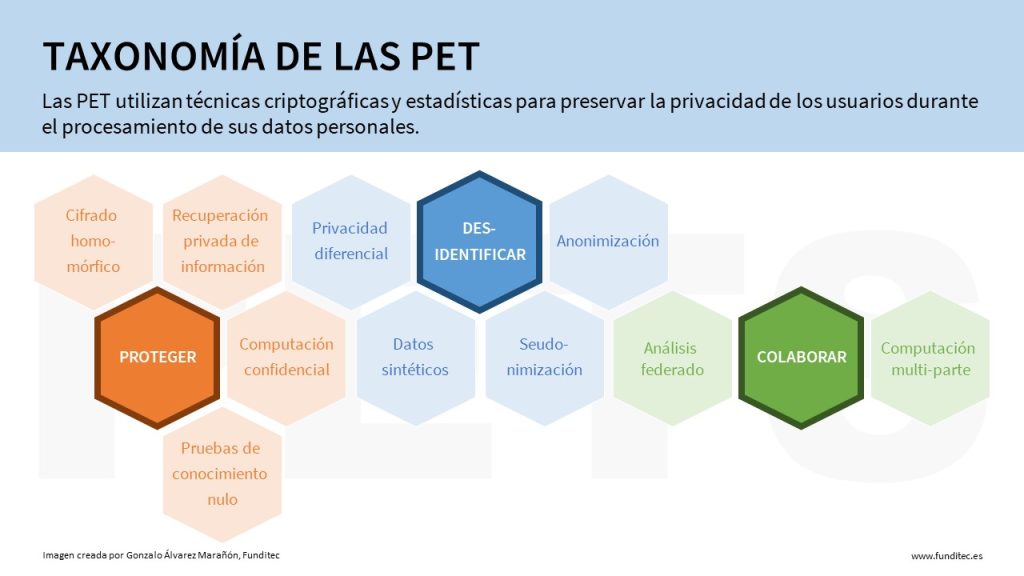
PET Taxonomy
PETs can be categorized into three areas depending on their focus:
- Protection techniques: They use unconventional cryptographic algorithms to make personal data inaccessible to third parties.
- Null knowledge proofs- When users can demonstrate their knowledge of a value without revealing the value itself.
- Confidential computing– Hardware-based Trusted Execution Environment (TEE) as a secure enclave within a CPU.
- Homomorphic encryption: when data is encrypted before sharing it, so that it can be analyzed, but without decrypting the original information.
- Private information recovery- When a user wants to obtain information from a server without the server knowing what information it has given to the user.
- De-identification techniques- reduce the amount of personal data that is collected or processed.
- Differential privacy: add random additional data (noise) to a data set to make it impossible to obtain information about individual entries.
- Anonymization: eliminate the direct, or indirect, identifiers of a data set through a manual or automated process.
- Pseudonymization: replace an element of data, such as an identifier, by a non-sensitive equivalent in a reversible or irreversible way: such as tokenization, masking or generalization.
- Synthetic data: create entirely new synthetic data, typically using machine learning, that mimics the characteristics of real-world data.
- Collaboration techniques- Share knowledge learned from different sources without sharing the data used to acquire it.
- Secure multi-party computing: When data analysis is spread across multiple parties, such that no single party can see the entire data set.
- Federated analysis: where parties share information obtained from the analysis of their data without sharing the data itself.
Uses and applications of PET
PETs are being used in a variety of real-world applications to protect user data privacy:
- Cloud computing services- To protect users' personal data stored in the cloud using confidential computing or homomorphic encryption.
- Digital advertising and recommendation systems: to limit the amount of personal data collected from users for advertising purposes or to recommend products, for example, using anonymization techniques to hide the identity of the users to whom the advertisements or recommendations are directed.
- Scientific investigation: to protect the personal data of research subjects through federated learning techniques.
- Cybersecurity: to exchange cyber intelligence data between multiple disparate organizations, so that although each organization can only see its own, searches can be run on the whole.
- Cryptocurrencies: The best example is Zcash, a cryptocurrency focused on ensuring the privacy and anonymity of its users. To achieve this, Zcash employs a specialized variant of null-knowledge proofs, called zk-SNARK.
The British Government has published a Guide for the adoption of PETs very complete and didactic, which includes an extensive list of use cases, as well as a flow chart to assist in the selection of the most appropriate PET technique depending on your particular use case.
The future of PET and privacy in relation to AI
The advance of AI is unstoppable and its voracity for personal data will only grow, which will predictably increase the demand and need for increasingly robust and sophisticated PETs. Additionally, government regulations, such as the General Data Protection Regulation (GDPR) in Europe, will play a crucial role in how companies implement and adopt PET. It is essential that both organizations and individuals understand the importance of privacy in this AI-dominated world and act accordingly.
The more concerned you are about the privacy of your own personal data, the more regulatory pressure governments will put on companies and the more demand for new and better PET techniques will grow, which in turn will encourage research in this fascinating field.
Value and protect your privacy. We will all win.
Learn in our Professional Master in Cybersecurity, Ethical Hacking and Offensive Security.



































