A new phishing campaign has appeared distributing the ZLoader malware using documents Microsoft Office as a Trojan horse to access our system, according to a report generated by the security firm Forcepoint X-Labs.
To train you in Cybersecurity and be able to aspire to positions of Address in the area of cybersecurity and of expert in Informatic security With solid technological and managerial knowledge, the Master in Cybersecurity, Ethical Hacking and Offensive Security You will train with specialized professionals.
Phishing attacks
The phishing attacks are the order of the day, normally, they try to access our systems by posing as a trusted company or organization (Netflix, Amazon, DGT, electricity companies, etc.) so that in this way the victim trusts and downloads the file with malware.
The report describes the malicious attachment in these emails as a Microsoft Word attachment in MHTML format with a randomly generated file name. MHTML is a web page archive file format that is compatible with web-based technologies.
In this case the phishing emails They use a billing decoy, the message may vary, but the purpose is the same, for the user to download the office file.
If the phishing victim, by downloading and opening the Microsoft Word attachment, you will enable the macros, triggers the download of an encrypted Excel sheet in which the final payload of the malware is hidden.
“After downloading the XLS file, Word VBA reads the cell content from XLS and creates a new macro for the same XLS file and writes the cell content into XLS VBA macros as functions.” They said researchers. “Once the macros are written and ready, the Word document sets the registry policy to 'Disable Excel Macro Warning'. It then invokes the malicious macro function from the Excel file. The Excel file now downloads the ZLoader payload. The ZLoader payload is then executed using rundll32.exe.”
Example of malicious attachment
ZLoader is a multipurpose trojan which often acts as a dropper delivering Zeus-based malware in multi-stage ransomware attacks, such as Ryuk and Egregor.
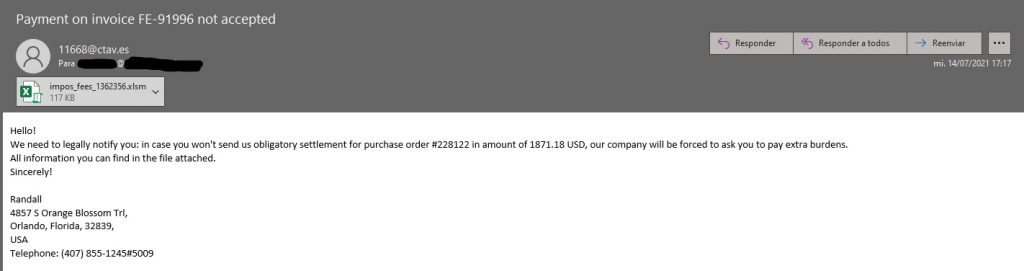
As we can see in the image that a colleague has sent us, the subject indicates “Payment for invoice FE-91996 is not accepted” and then in the body of the message they tell us that we owe that invoice and that we must pay it before it is generate additional expenses, inviting us to open the file where we can see all the information.
We keep biting
The email scams invoicing are still effective since the targeted victim of phishing is likely to be receptive to anything to do with unpaid invoices and even returns.
Malware has become increasingly difficult to detect and information theft will be inevitable if we do not raise awareness and acquire a daily cybersecurity routine.
We recommend that you go through this post where we give you 5 cyber commandments to improve your cybersecurity.



































