1. CISO, INNOVATION AND DIGITAL TRANSFORMATION
The innovation, according to the RAE, is the “action and effect of innovating” (that is, introduce new things). It is also defined as the “creation or modification of a product, and its introduction into a market”. We can understand innovation using disruptive digital technologies as an approach to the current concept of digital transformation.

Currently, organizations are immersed in processes of digital transformation, where they adopt disruptive technologies to obtain competitive advantages for them, making profound changes in the business and culture of the organization.
In the interconnected world in which we live, talking about computerizing businesses is a thing of the past, since we will hardly find a business that currently does not have an automated or digitalized part. We cannot consider this digital transformation if it has not involved a profound change in the way of working or a redesign of its processes using technologies such as:
- Cloud Computing
- Big Data
- Artificial Intelligence (AI)
- Internet of Things (IoT)
Other disruptive technologies that may be present in digital transformation processes are: Web 3.0, Blockchain, DevOps, 5G, Quantum Computing, Metaverse, etc.

Digital transformation requires a redesign of products, strategies and processes principals of organizations by taking advantage of digital technology, for which a cultural change normally led by the Executive Director or CEO (Chief Executive Officer), of the organization. Digital transformation is not a project, it is a process, so it never ends and should be guided by continuous improvement.
Digital transformation involves completely rethink an organization, since it is a process that consists of reorienting an organization towards the application and use of emerging digital technologies in the organization's key processes.
That said, not all organizations are prepared for a radical change like this, as it requires a process of cultural change, organizational change and finally application of technology throughout the organization.
Are examples of public digitalization strategies:
- Digital Spain 2026: Roadmap for the country's digital transformation. 50 measures that are articulated around 10 strategic axes (one of them “Cybersecurity”). https://portal.mineco.gob.es/es-es/ministerio/estrategias/Paginas/00_Espana_Digital.aspx
- Digital European Compass 2030: The European Commission proposes a digital compass that evolves around 4 cardinal points.
He ultimate goal of digital transformation in organizations is survive in an unpredictable and increasingly competitive and fast environment. But, what is the role of cybersecurity within digital transformation processes?
2. CYBERSECURITY IN DIGITAL TRANSFORMATION PROCESSES
2.1 GOVERNANCE IN CYBERSECURITY
The digital transformation is affecting all entities, both public and private, and all the critical processes of businesses that want to be competitive, so roles such as the Head of Information Systems or CIO (Chief Information Officer), together with those responsible for the different business areas, are essential for digital transformation processes to be a success.
But what about the Chief Information Security Officer or CISO (Chief Information Security Officer)? What role does it play in digital transformation?
An example of digital transformation could be the implementation of smart cities (Smart Cities) where the digitalization and sensorization of cities, together with technologies such as AI or Cloud Computing, are used as a basis for the governance of the city, generating a higher quality of life for the citizens who live there.
What would happen if traffic lights were easily controllable by unauthorized people? What if energy systems suffered a cyber attack and left a large city without power? What if the water company's industrial control systems were manipulated or public transportation paralyzed?

A world where “almost everything is digital” requires a Appropriate cybersecurity governance and information security management based on ICT risks.
Therefore everything information security governance model should clearly identify the following blocks of responsibility:
- Government: represented by the Information Security Committee that is established, the CEO and those responsible for the business areas (responsible for information and services).
- Supervision: represented by the organization's CISO (responsible for security) and, if applicable, the DPD (Data Protection Officer) as an advisor on data protection matters.
- Operation: represented by the organization's CIO (responsible for systems).
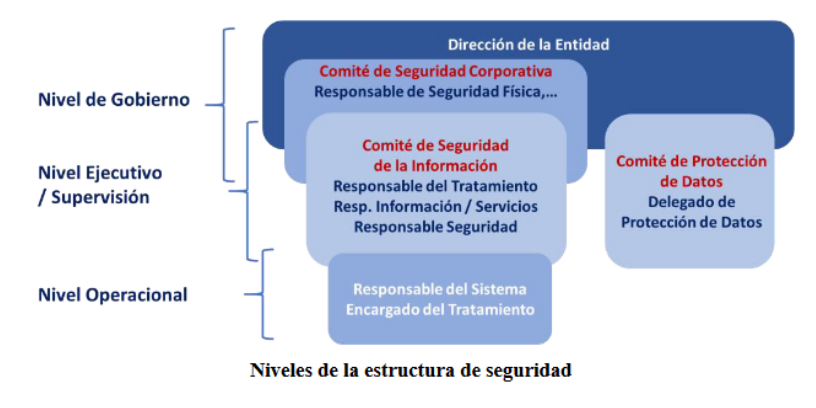
Whether in traditional systems or within digital transformation processes, a clear separation of functions must be maintained, especially the “security as a differential element” versus the operation of the systems, so the governance model chosen is key to the success of the implementation of the digital transformation process.
2.2 CHALLENGES OF CYBERSECURITY IN DIGITAL TRANSFORMATION
Due to the complexity of digital transformation processes, we can identify the following challenges to address in terms of cybersecurity:
- Increase in the attack surface: the perimeter is no longer defined and own infrastructure is mixed with interconnected external services. The greater the exposure surface, the greater the ICT risks and the possible vulnerabilities to exploit. Furthermore, different technologies generate different vulnerabilities and risks.
- More sophisticated cyberthreats: cybercriminals adapt to technology, generating more sophisticated, more frequent threats with greater impact (CaaS – Crime as a Service, APTs – Advanced Persistent Threats, etc.).
- Convergence of IT and OT: due to the development of industry 4.0 and industrial IoT, information security must be comprehensive (physical and digital security).
- Greater interrelationship and dependency with third parties: therefore control of cybersecurity in the supply chain is essential. Shared versus delegated responsibility is desired. External incident management needs to be agreed upon, as well as balancing cybersecurity maturity levels between entities (contractor and contracted).
- Alert fatigue: we have more and more alerts from different sources, with great difficulty in interpreting them, measuring them, correlating them and ruling out false positives. You need to prioritize and obtain quality information to make the right decisions.
- Regulatory complexity: information security management has extensive sectoral regulation that requires extensive technical, legal and management knowledge for the correct protection of information and digital services (GDPR, ENS, NIS, NIS2, DORA, PCI-DSS, etc.)
- Limited resources: few cybersecurity specialists, limited budget, little time for so many open fronts and the need to hire 24x7 managed security services.

Cybersecurity must be a transversal part of the digital transformation processes and requires:
- Cybersecurity by design (Security by design): cybersecurity as a competitive advantage involved in making strategic digital transformation decisions from the beginning.
- Automation and cyber intelligence: using the maximum possible automation as well as AI solutions to detect attack patterns and correlate alerts and behaviors.
- Prevention, detection and response to cyber incidents: for correct management of cyber incidents and an adequate SOC, with specialized teams and 24x7 services.
- Centralized and standardized asset repository, as well as a vulnerability database: to be able to apply automation and cyber intelligence to vulnerability management and cyber incident management.
- Integration of physical and digital security: an interaction between physical systems and cyberspace is desirable as part of IoT and OT integration.
- Managed security and as a service: security as a process of continuous improvement within an information security management system (ISMS) that helps decision making and justifies investments in cybersecurity.

Cybersecurity must be part of the digital transformation strategy of organizations since digital dependence is total and without cybersecurity, companies are exposed to both cyber attacks and large sanctions for regulatory non-compliance that can end the business (possible reputational damage, extortion due to data theft, unavailability of services, etc. ).
2.2 THE ROLE OF THE CISO IN DIGITAL TRANSFORMATION
In organizations with a certain level of maturity in cybersecurity, the role of the CISO (responsible for security) must be totally differentiated from the role of the CIO (responsible for systems). They are complementary roles but each one has well differentiated functions.
There are legal frameworks that require such separation of duties. For example, the National Security Scheme (Royal Decree 311/2022) explicitly says that “The responsibility for the security of the information systems will be differentiated from the responsibility for the exploitation of the information systems concerned.”. Therefore, the CISO must be separated from the operation of the systems and should act as a translator between the importance of business processes and the digital systems that support them.
Those responsible for business processes will convey to the CISO the importance of their processes (information and services) and The CISO will translate said criticality into security measures (technical and organizational) that the organization will have to implement so that its information systems are at security (or risk) levels acceptable to the organization.

That is why the most relevant functions of the CISO are:
- Define and align the cybersecurity strategy with the company's objectives.
- Analyze and manage the organization's ICT risks.
- Define security regulations.
- Prevent, detect, analyze vulnerabilities and manage cyber incidents.
- Train and raise awareness in the organization regarding information security.
- Inform and report to management on security indicators and status.
In order to add value to digital transformation processes The CISO will have to increase and strengthen some of its capabilities:
- Relationship: must have leadership, communication, team management and business understanding skills.
- Management: you must use indicators and promote an information security management system for cybersecurity decision making.
- Techniques: you must anticipate training in the disruptive technologies selected within the organization's digital transformation (Cloud, AI, IoT, 5G, etc.).

In summary, the role of the CISO in digital transformation (TD) must cover the following aspects:
- Security as a strategic advantage: you must participate in the decision processes and prepare the organization to achieve digital transformation objectives, aligning cybersecurity with business objectives.
- Involved from the earliest phases of the digital transformation, you must go from being a spectator to being a proactive element in all phases of the TD process:
- Before starting the process: with active participation in the definition.
- During the process: providing differential value at all levels.
- Once the process is implemented: through governance, risk and compliance (GRC).
- Risk-oriented: by making decisions based on the organization's risk appetite (formalized and accepted by management).
- With “hard” skills (hard skills): through continuous technological updating (Cloud security, DevSecOps, API Security Frameworks, Zero Trust, AI, RPA, etc.)
- With “soft” skills (soft skills): being an enabler of change committed to the management strategy. Good communicator and translator between the business and digital systems, generating value and understanding at all levels of the organization.
We must not forget that within the digital transformation processes the CISO must have a proactive role It should not be seen as an element of friction/slowdown of the organization's digital transformation.
To learn everything you need, take into account our Professional Master in Cybersecurity Management, Ethical Hacking and Offensive Security.



































