The Deep and Dark web
They are two concepts that are quite related for most people. You automatically think of (cyber)crime, drugs, weapons and a long list of criminal elements. People who have that in mind are simply wrong. The reality is that both concepts do not necessarily have anything to do with each other. It could be said that they are only united by the fact of being part of the immense and infinite cyberspace.
On the one hand, the Deep Web It is that part of the Internet that you enter using any conventional browser and after passing some kind of authenticationFor example, the personal bank account, the Amazon account, Telegram, WhatsApp... What's criminal there?
On the other hand, we have the Dark Web, that part of the internet is not as easily accessible as the previous one. In this case, a special browserFor example, the well-known Tor Browser. In this Dark Web we have many resources and they are all common to those that we can find in both the Surface and Deep Web, the only difference would be that the browsing is anonymous.
As with everything, if someone wants, they can take advantage of it to do evil. But this happens on the street, as well as on the internet, whether Surface, Deep or Dark Web. The fact is that, since someone wants to use the Internet to commit a criminal act, they will try to hide as much as possible. And how do you get that? Making use of the darknets available, such as the Tor network.
On the Dark Web you can find everything humanly imaginable. starting with the best known as they can be drugs and weapons, passing through services of hackers malicious and purchase of money fake and ending with the purchase of organs for transplants, hiring hitmen, kidnappings, And a long etcetera.
The cradle of cybercrime
In this article we focus on the threat actors who take advantage of this anonymous network to create their own cybercrime niches.
A threat actor is a real individual, group or organization that operates with malicious intentions and different motivations such as political, economic or protest, among others.
Markets
These threat actors operate regularly and openly on the Dark Web. One of the most common platforms in this type of darknets are Markets of access credentials obtained by botnet-type malware. There are countless of them, however, one of the best known is Genesis Market. The prices of this Market range between approximately five and 150 dollars per set of credentials and offer the possibility of searching by website or by type of platform. For example, doing a search for Amazon credentials obtained in Spain.
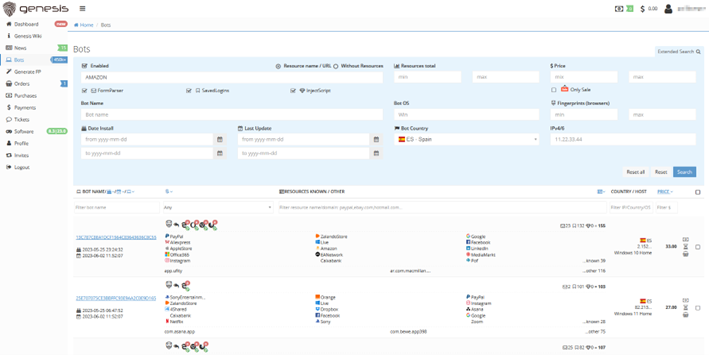
Once the credentials pack is accessed, all kinds of useful information appears, including:
- He country of origin of the affected system
- The first two octets of the IP adress
- He OS of the affected device
- All the domains for which malware has stolen credentials
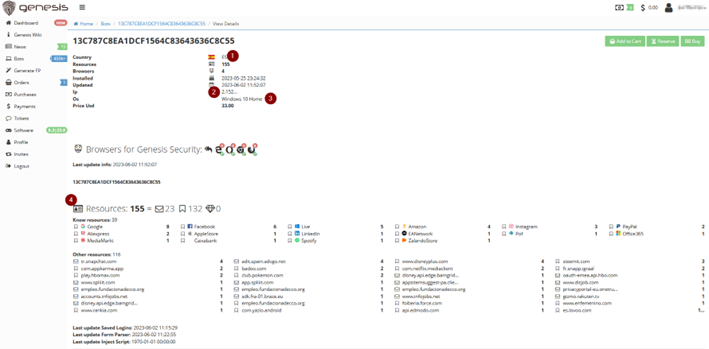
In this example above, all credentials would be sold for $33.
Forums Underground
On the other hand, there are the famous forums underground where you can also find everything, however, the most difficult thing is the sales of RDP type accesses (Remote Desktop Protocol), VPN (Virtual Private Network), accounts Domain Controllers, of Active Directory, etc.
Many threat actors gain this type of access and use it to enter companies' infrastructure and carry out attacks, usually ransomware. Other threat actors only obtain them and then offer them for sale for amounts of money that range from one hundred dollars and can sometimes reach up to two hundred thousand dollars. Of course, access to a network from a large company is not the same as access to a much smaller one since the gain in case of success will also be proportional.
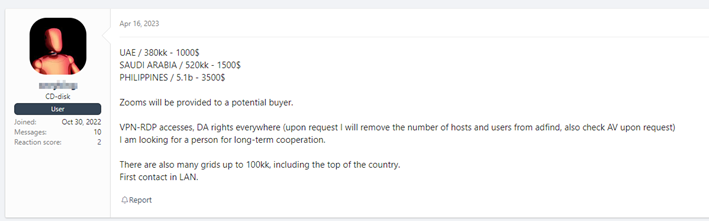
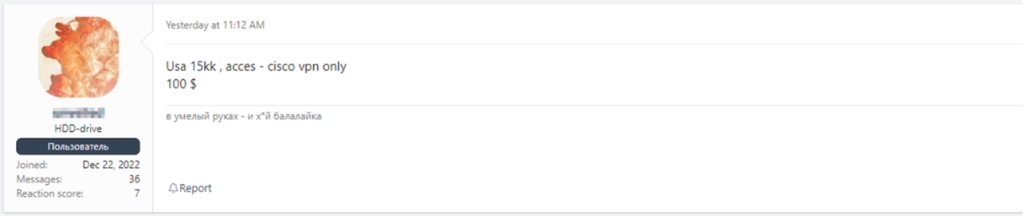
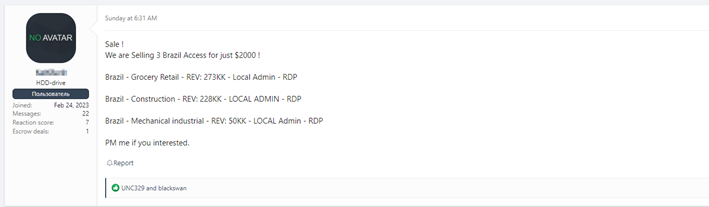
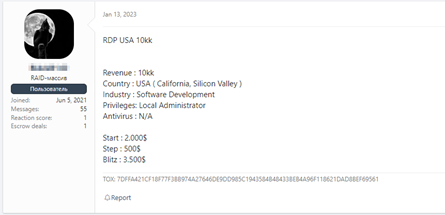
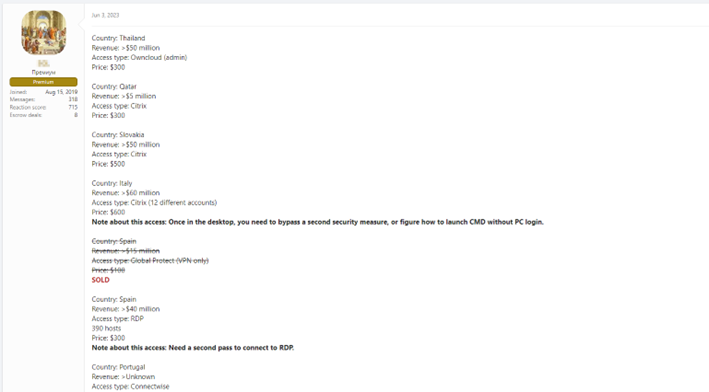
All are examples of access sales in Deep and Dark Web forums. As you can see, the threads are updated regularly, even indicating what has already been sold at a given time and is no longer available.
Ransomware groups
Something that has resonated a lot since the pandemic in 2020 are ransomware groups and their walls of shame or “Hall of shame”. Ransomware groups use these platforms to openly publish the information of victims of threat actor groups who have hijacked and/or encrypted their information.
Among the most common ransomware groups we have Lockbit 3.0, BlackBasta and Play Ransomware. Each and every one of them offers their exfiltration website so that whoever wishes can access and view the data stolen from their victims.
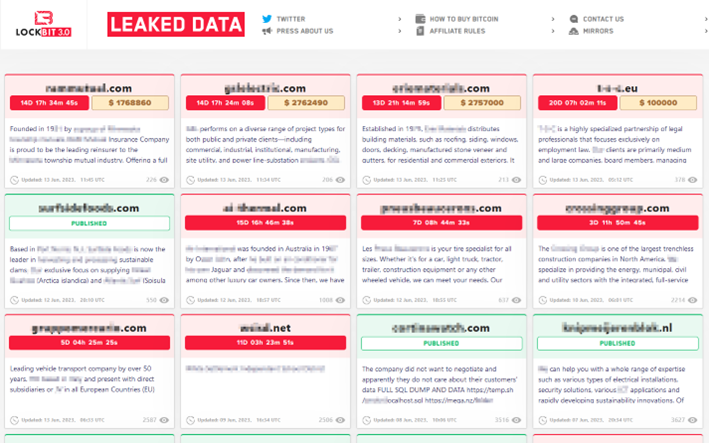
Illustration 1. Lockbit Wall of Shame.
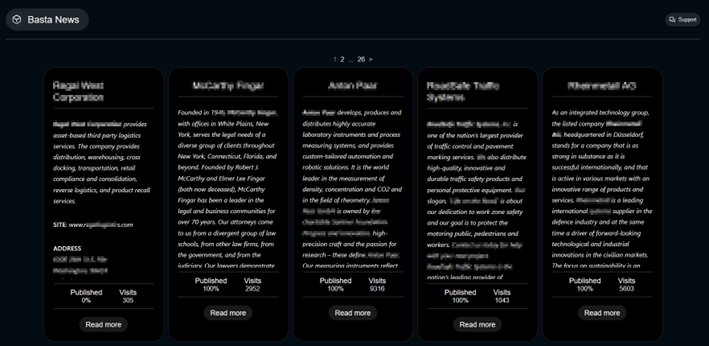
Illustration 2. BlackBasta Wall of Shame
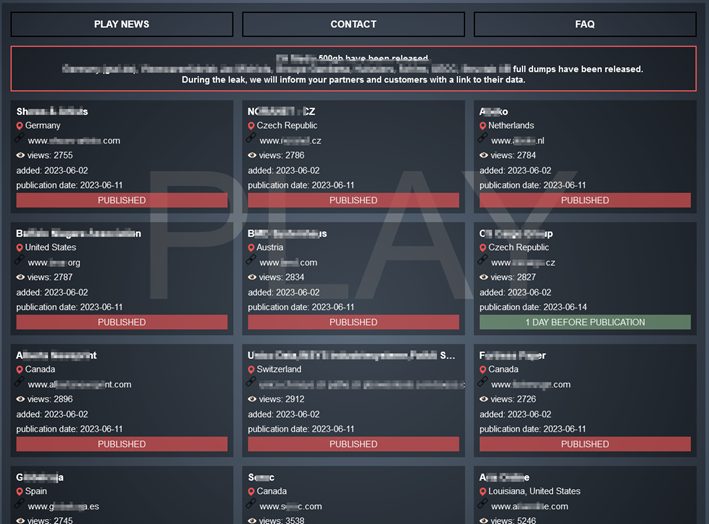
Illustration 3. Play Ransomware wall of shame.




































Marta, congratulations on your excellent article and your great work on the master's degree. Professionals like you make it worth doing.